
INFORMATION TECHNOLOGY
Our strength is derived from our team of highly certified professionals. Our experts work closely with our customers to understand their IT needs and challenges, and then provide the right solutions. No matter what your needs are, ISG can help to complete your projects successfully
System Integration
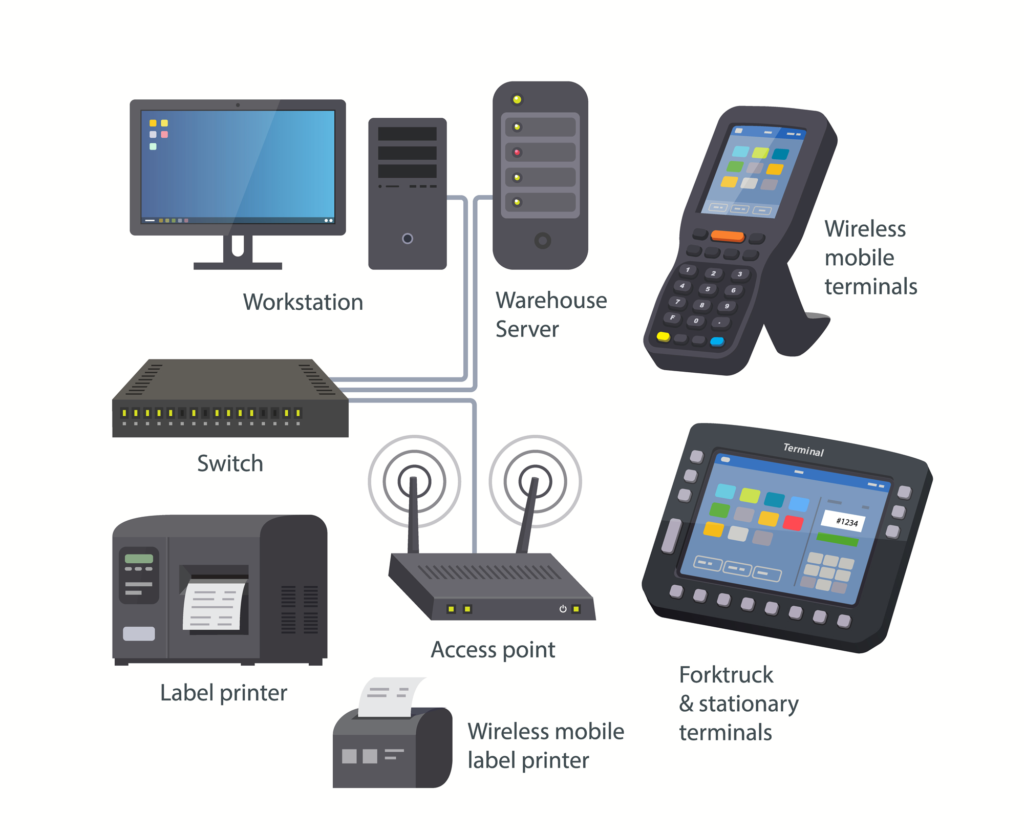
To ensure a successful integration project, ISG adheres to the following best practices from day one:
- Define user needs, roles and permissions
- Enable non-repudiation
- Document edge case protocols
- Build-in security from the ground up
We believe that addressing these core issues will provide higher success rates at the end of a project.
User Needs, Roles and Permissions
From the start, there needs to be clarity about what user needs the integration is trying to solve and how they match up with different roles.
Otherwise, the systems integration might give certain users too much or too little flexibility to meet its objectives. That could require potentially time-consuming and expensive fixes down the line.
Non-Repudiation – (unable to deny)
It’s critical to verify that messages between systems are sent and received. Otherwise, important information could be missing without anyone being aware.
Edge Case Protocols
When something does go wrong, ISG ensures that there is clear documentation about how to resolve the issue.
System Security
Security needs to be part of the DNA of any company’s IT s culture. When it comes to software, every string of code is a window for hackers. We do not wait until the QA phase to secure it. We ensure that the solution is built secured from the ground up.
